Update, May 12, 2020. In response to this work, Cisco has made some improvements related to transparency. Read about the details.
The Webex-specific policy discussed in this post is now presented to users at the account creation page. This is a good improvement by Cisco. This post has been updated to reflect Cisco’s changes by adding ̶s̶t̶r̶i̶k̶e̶t̶h̶r̶o̶u̶g̶h̶ ̶t̶e̶x̶t̶ to indicate updated content. End update.
— — — — — — — — — — — — — — —
This policy overview for Webex is part of a series looking at the privacy practices of commonly used videoconferencing services.The series includes:
- Introduction — the introduction provides background information on the scope of this work, and a summary of general findings
- An overview of Google Meet, Duo, and Hangouts
- An overview of Microsoft Skype and Teams
- An overview of Cisco WebEx (this document)
This policy overview for Webex has three sections:
- Summary Notes, general observations about the privacy policy and service offering;
- Rubric Mapping, a more structured look at the services, mapping the language in the privacy policy to 10 defined categories; and
- Policy Notes, a series of excerpts from the privacy policy, with commentary on what the language means.
The privacy policy analysis is based on the publicly available policy at https://www.cisco.com/c/en/us/about/legal/privacy-full.html.This policy was last updated on December 23, 2019. In this overview, this privacy policy is referred to as the “main privacy policy” or the “main policy.” Cisco refers to this document as the “Privacy Statement.”
The policy document at https://trustportal.cisco.com/c/dam/r/ctp/docs/privacydatasheet/collaboration/cisco-webex-meetings-privacy-data-sheet.pdf is also considered, although this document is not presented to end users at the time of account creation. The fact that this document is not presented to end users during the account creation process raises an interesting question: can an end user consent to terms they don’t know exist? The document at the above link is labeled as version 4.0, updated April 2020. In this overview, this document is referred to as the “Webex-specific policy” or “the secondary policy.”
1. Summary Notes
1. ̶T̶h̶e̶ ̶r̶e̶l̶e̶v̶a̶n̶t̶ ̶p̶r̶i̶v̶a̶c̶y̶ ̶p̶o̶l̶i̶c̶i̶e̶s̶ ̶f̶o̶r̶ ̶W̶e̶b̶e̶x̶ ̶a̶r̶e̶ ̶n̶o̶t̶ ̶e̶a̶s̶y̶ ̶t̶o̶ ̶f̶i̶n̶d̶. The steps outlined below show a typical user path to policies starting from the account creation page linked from webex.com.
The sign in for webex is here: https://cart.webex.com/sign-up-webex.
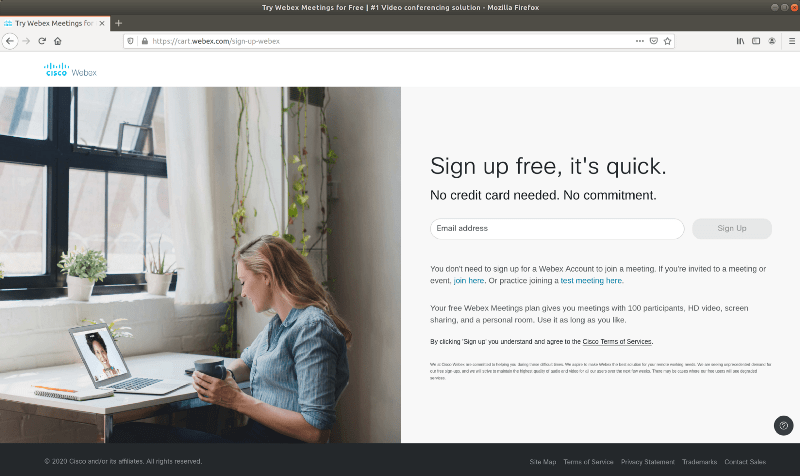
This sign up form links to the terms of service; the terms of service in turn reference the privacy statement, but the most obvious link to the privacy statement is in the right sidebar.
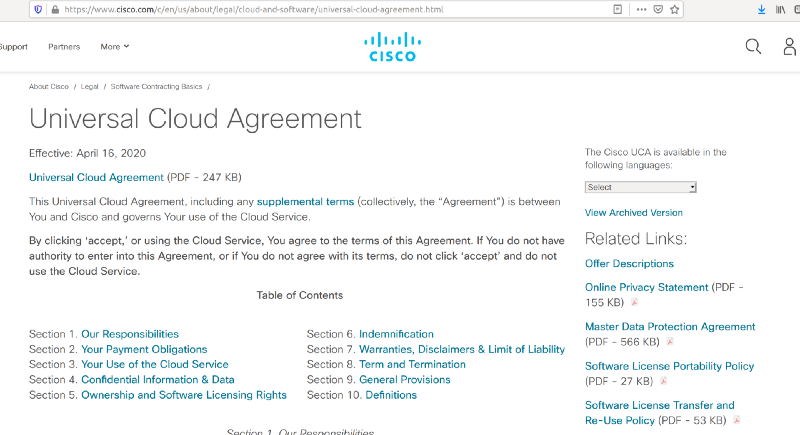
If you successfully find the main privacy policy, you also might be able to find the link to the “Privacy Data Sheets.” In the screenshot below, you can see it in the lower right corner of the image.
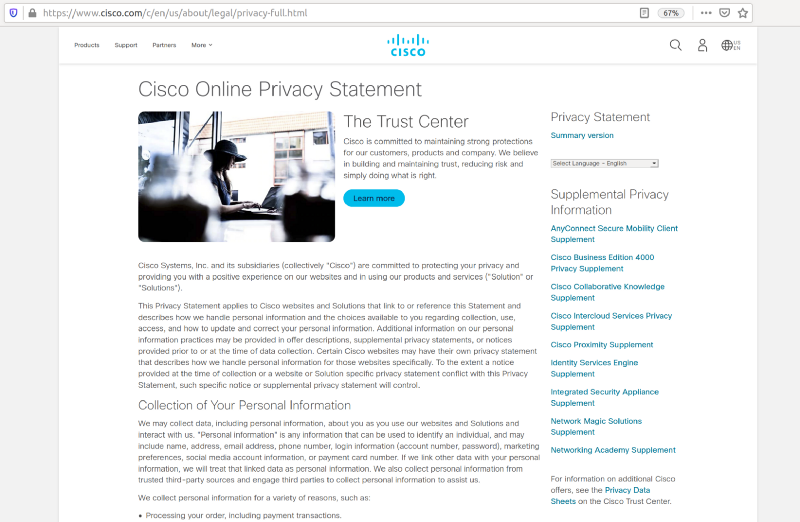
That link points to Cisco’s Trust Portal. The Trust Portal contains links to at least 81 different privacy documents. Apparently, there’s a lot to trust.
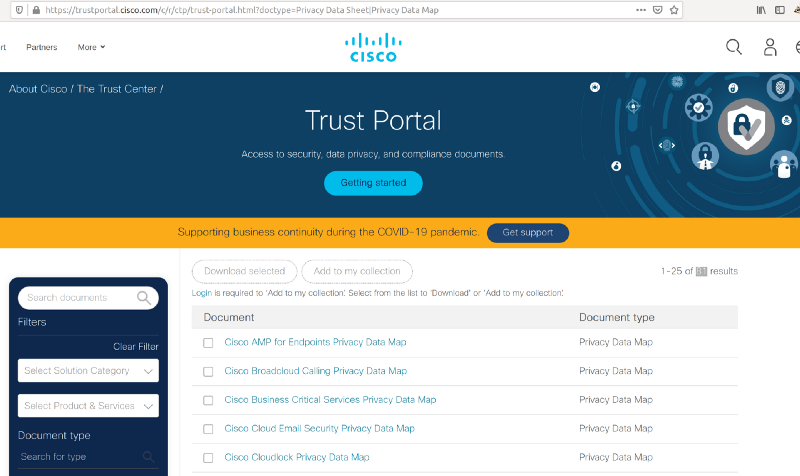
Filtering by “Webex” brings the list down to 13 documents.
These documents contain useful information, ̶b̶u̶t̶ ̶t̶h̶e̶y̶ ̶a̶r̶e̶ ̶n̶o̶t̶ ̶p̶r̶e̶s̶e̶n̶t̶e̶d̶ ̶t̶o̶ ̶a̶ ̶p̶e̶r̶s̶o̶n̶ ̶i̶n̶ ̶a̶n̶y̶ ̶m̶e̶a̶n̶i̶n̶g̶f̶u̶l̶ ̶o̶r̶ ̶a̶c̶c̶e̶s̶s̶i̶b̶l̶e̶ ̶w̶a̶y̶. One of the 13 documents contains additional information about how Cisco Webex Meetings processes data. That document is included in our analysis below, but the idea that a normal person signing up for Cisco services could find — or consent to — this document is questionable at best.
The route to relevant privacy documents should be more direct. Cisco should include a direct link to all relevant policy documents from all account creation pages, and both the terms of service and privacy policy should contain clear, direct, and obvious links to other relevant privacy documentation.
2. Cisco’s main privacy policy does not contain words generally associated with videoconferencing (conference, audio, recording, meeting, group). The word “video” is used once, but not in reference to videoconferencing. One possible reason for this is that the terms were designed to be general and cover multiple different types of products, but it is difficult to understand the privacy implications of a videoconferencing service when video isn’t mentioned.
3. Cisco’s terms note that they might add additional information about privacy practices within applications, or at the point of data collection. Practically, this has the potential to make it impossible to understand the privacy risks or privacy protections connected to using a service before using the service because the full range of any risks or protections are not fully disclosed ahead of time.
4. Cisco’s terms state that Cisco can get additional information about users of their products, including Webex, from third parties.
5. Cisco’s terms state that Cisco uses third parties to gather data about end users, and the main privacy policy is not explicitly clear about what limits, if any, exist on how third parties can use the data they collect for Cisco.
7. Cisco’s main privacy policy defines data collected as an asset that can be shared or transferred, with no notice to end users.
8. Cisco’s main privacy policy does not define any clear data sunsets. Their terms contain general language that could potentially be interpreted as allowing them to retain data indefinitely. Their secondary policy defines sunsets that can stretch to up to 7 years. This lengthy time period, combined with the broad rights claimed to share data with third parties and with Cisco’s treatment of data as an asset that can be transferred as part of a sale without notice, creates a significant privacy risk.
2. Webex mapped to the Rubric
This rubric is based on the policy notes included below in Section 3.
Personal Data Leak
Webex, like all videoconferencing services, have the potential for leaking personal data. Hosts can record calls and potentially share those recordings, and other participants can make surreptitious recordings of calls without the knowledge or consent of participants.
When participating in any videoconference, if you are not aware whether or not a call is being recorded, ask the host. If it is not possible to ask the host, assume that the call is being recorded, and adjust your level of participation in the call to whatever feels comfortable.
First Party Data Collection
Cisco’s terms note that they might add additional information about privacy practices within applications, or at the point of data collection. Practically, this has the potential to make it impossible to understand the privacy risks or privacy protections connected to using a service, because the full range of any risks or protections are not fully disclosed ahead of time.
Data Enhancement
Cisco collects information about end users from third parties. Cisco also uses third parties to collect information from end users. In both cases, the third parties do not appear to be listed. In the case of the third parties that Cisco allows to collect information, there does not yet appear to be any limits placed on how they can use the information they collect.
Additionally, Cisco’s main privacy policy states third parties that collect information may also combine information about end users from other sources. This has the potential to create a large trove of data on anyone who touches a Cisco service.
Third Party Access
Cisco’s main privacy policy states that they will share personal information with third parties for the marketing purposes of the third parties. Given that Cisco defines personal information to include the information they collect, and data that they receive from third parties, the subsequent re-disclosure of that information could be outside of what people using a service would reasonably expect. If this is not a standard practice for Cisco products, or if specific Cisco services are exempt from this type of sharing, Cisco should link to specific policies and make these commitments to users at the point when a user creates an account for the service.
Implications of Employer or School Sponsorship of Service
Cisco’s main terms do not contain clear or obvious descriptions about what hosts or employers can see, but their secondary policy describes how employers can access specific information about their employees. The secondary policy also describes an optional feature called “People Insights” that aggregates and displays information about conference participants such as employment history, education history, and publicly available social media posts.
Data Deletion and Retention
Cisco’s main terms do not define any clear data sunsets. Their main terms contain general language that could potentially be interpreted as allowing them to retain data indefinitely. Cisco also shares a secondary policy that indicates that, in many cases, Cisco can retain data for up to 7 years. The ability to retain data for years, paired with the broad rights claimed to share data with third parties, paired with Cisco’s treatment of data as an asset that can be transferred as part of a sale without notice, creates a significant privacy risk.
Differentiation between data collected from hosts versus participants
Cisco’s main privacy policy does not contain words generally associated with videoconferencing (conference, audio, recording, meeting, group). The word “video” is used once, but not in reference to videoconferencing. Cisco has a range of additional documents that are not directly presented to end users that contain more detailed information about data collection practices.
Information Used for Product Improvement
Cisco claims broad rights over how it can use personal information, including for marketing, operating their business, and product improvement.
Data That Can Be Sold or Shared as Part of a Transaction
Cisco’s terms define data collected as an asset that can be shared or transferred as part of several different transactions or reorganizations. The language around data transfers does not mention any need to notify or inform end users.
Access to Data for Machine Learning, AI Analysis, or Human Review
Cisco’s privacy policy does not contain significant details on any use — or limits placed on use — of data they collect for tuning or developing automated data analysis. A secondary policy that describes Webex-specific features describes how Webex can use data for facial recognition if a user opts in to the usage.
3. Policy Notes
The rough notes below include direct quotations from Cisco’s Main Privacy Policy, a second Webex-specific policy, and commentary on the potential implications of the policy language. These notes are not legal advice.
The larger excerpts of policy language are in italics.
Main Policy
— — — — — — — — — — — — — — — –
First Party Collection
Cisco’s terms note that they might add additional information about privacy practices within applications, or at the point of data collection. Practically, this has the potential to make it impossible to understand the privacy risks or privacy protections connected to using a service, because the full range of any risks or protections are not fully disclosed ahead of time.
“Additional information on our personal information practices may be provided in offer descriptions, supplemental privacy statements, or notices provided prior to or at the time of data collection. Certain Cisco websites may have their own privacy statement that describes how we handle personal information for those websites specifically. To the extent a notice provided at the time of collection or a website or Solution specific privacy statement conflict with this Privacy Statement, such specific notice or supplemental privacy statement will control.”
— — — — — — — — — — — — — — — –
First Party Collection
Cisco’s definition of personal information is fairly general and broad, and this has the potential to offer additional protection to the data held by Cisco. If additional protections are offered, this is a good thing. If there are broad rights to disclose, share, or transfer personal information, then the broad definition of personal information has negative implications for privacy.
“We may collect data, including personal information, about you as you use our websites and Solutions and interact with us. “Personal information” is any information that can be used to identify an individual, and may include name, address, email address, phone number, login information (account number, password), marketing preferences, social media account information, or payment card number. If we link other data with your personal information, we will treat that linked data as personal information.”
— — — — — — — — — — — — — — — –
Data Enhancement
Third Party Data Collection
Cisco collects information about end users from third parties. Cisco also uses third parties to collect information from end users. In both cases, the third parties do not appear to be listed. In the case of the third parties that Cisco allows to collect information, there does not yet appear to be any limits placed on how they can use the information they collect.
“We also collect personal information from trusted third-party sources and engage third parties to collect personal information to assist us.”
Additionally, the third parties that collect information may also combine information about end users from other sources. This has the potential to create a large trove of data on anyone who touches a Cisco service.
“We and the third parties we engage may combine the information we collect from you over time and across our websites and Solutions with information obtained from other sources. This helps us improve its overall accuracy and completeness, and also helps us better tailor our interactions with you.”
— — — — — — — — — — — — — — — –
Product Improvement
Cisco claims broad rights over how it can use personal information, including for marketing, operating their business, and product improvement. The language does not explicitly mention targeted advertising, but the terms are adequately broad to the point where behavioral profiling and/or targeted advertising could occur.
“We may use your personal information for the purposes of operating our business, delivering, improving, and customizing our websites and Solutions, sending marketing and other communications related to our business, and for other legitimate purposes permitted by applicable law.”
— — — — — — — — — — — — — — — –
First party collection
Cisco acknowledges that, in some cases, they act as a data controller. However, they do not specify when that is — or when that isn’t — in play. Because of this lack of clarity, it is not possible to know when a person can access the rights that Cisco describes.
“Some Cisco entities may act as or be considered “data controllers”. When a Cisco entity is acting as a data controller, you can exercise your rights of access and request corrections, suppression, or deactivations under applicable data protection laws directly with that Cisco entity as described in the specific Solution documentation.
If you need additional assistance, or help with accessing, correcting, suppressing, or deleting your personal information, please feel free to contact us directly. We make good faith efforts to honor reasonable requests to access, delete, update, suppress, or correct your data. We will respond to your request within 30 days. If we are unable to honor your request, we will provide you with an explanation.”
— — — — — — — — — — — — — — — –
Third Party Access
Cisco’s terms state that they will share personal information with third parties for the marketing purposes of the third parties. Given that Cisco defines personal information to include the information they collect, and data that they receive from third parties, the subsequent re-disclosure of that information could be outside of what people using a service would reasonably expect. Additionally, the terms are not especially clear: they mention that sharing will be done “(w)ith your permission”, but then they state that a person needs to opt out of sharing by sending an email to Cisco’s privacy contact.
“With your permission, we may also share your personal information with Cisco business partners or vendors, so they may send you information about products or services that may be of interest to you. To opt-out of Cisco sharing with third parties for their marketing purposes, please send an email to privacy@cisco.com .”
— — — — — — — — — — — — — — — –
Third Party Access
Cisco’s terms repeat that they will share personal information with third parties. The only way to stop this sharing is to opt out, but to opt out a person needs to know about the sharing, and aside from reading the entire privacy policy it’s not clear how a person would know to opt out.
“We may share personal information in the following ways:
…
With Cisco business partners or vendors, so that they may share information with you about their products or services. To opt-out of Cisco sharing with third parties for their marketing purposes, please send an email to privacy@cisco.com.”
— — — — — — — — — — — — — — — –
Onward Transfer
Cisco’s terms define data collected as an asset that can be shared or transferred as part of several different transactions or reorganizations. The language around data transfers does not mention any need to notify or inform end users.
“We may share personal information in the following ways:
…
In connection with, or during negotiations of, any merger, sale of company assets, consolidation or restructuring, financing, or acquisition of all or a portion of our business by or to another company.”
— — — — — — — — — — — — — — — –
Legal Requests
Cisco’s terms define broad sharing of data with law enforcement and other “competent authorit(ies).”
“In response to a request for information by a competent authority if we believe disclosure is in accordance with, or is otherwise required by, any applicable law, regulation or legal process.
With law enforcement officials, government authorities, or other third parties as necessary to comply with legal process or meet national security requirements; protect the rights, property, or safety of Cisco, its business partners, you, or others; or as otherwise required by applicable law.”
— — — — — — — — — — — — — — — –
Data Retention
Cisco’s terms do not define any clear data sunsets. Their terms contain general language that could potentially be interpreted as allowing them to retain data indefinitely. This lack of a data sunset, paired with the broad rights claimed to share data with third parties, paired with Cisco’s treatment of data as an asset that can be transferred as part of a sale without notice, creates a significant privacy risk.
“We will retain your personal information as needed to fulfill the purposes for which it was collected. We will retain and use your personal information as necessary to comply with our business requirements, legal obligations, resolve disputes, protect our assets, and enforce our agreements.”
— — — — — — — — — — — — — — — –
Third Party Access
Cisco’s terms state that they can share information “(i)f we otherwise notify you and you consent to the sharing.”
Can Cisco provide an example of when they notified users when they shared information with a third party, and how they obtained informed consent?
— — — — — — — — — — — — — — — –
Cisco’s terms contain a section titled “Security of Your Personal Information” that contains bland and toothless language. However, Cisco also has a Master Data Processing Agreement that is pretty complete (at https://trustportal.cisco.com/c/dam/r/ctp/docs/dataprotection/cisco-master-data-protection-agreement.pdf) — Unfortunately, while the language in their Data Processing Agreement is solid, the document is clearly stamped as a “Reference” and appears to only apply a business customer has provisioned services from Cisco. If the provisions of that document are always in place, Cisco could incorporate it by reference, and offer some much needed improvements and clarity to their terms.
— — — — — — — — — — — — — — — –
Third Party Data Collection
Cisco’s terms state that they allow third party data collection. These third parties are not listed, and the opt outs are the generic industry-led option which only last if a person allows cookies, which then exposes the end user to more tracking.
“We partner with third parties to display advertising on our website or to manage our advertising on other sites. Our third-party partners may use cookies or similar technologies in order to provide you with advertising based on your browsing activities and interests. You may opt out of this advertising.”
— — — — — — — — — — — — — — — –
Personal Data Leak
Cisco’s terms define that any information shared in “forums” or “chat rooms” (which could theoretically extend to chat and messaging features in a video call) are the responsibility of the person who shares them.
“If you participate in a discussion forum, local communities, or chat room on a Cisco website, you should be aware that the information you provide there (i.e. your public profile) will be made broadly available to others, and could be used to contact you, send you unsolicited messages, or for purposes neither Cisco nor you have control over. Also, please recognize that individual forums and chat rooms may have additional rules and conditions. Cisco is not responsible for the personal information or any other information you choose to submit in these forums. To request removal of your personal information from our blog or community forum, contact us at privacy@cisco.com. In some cases, we may not be able to remove your personal information, in which case we will let you know if we are unable to do so and why.”
— — — — — — — — — — — — — — — –
Other
Cisco’s CCPA statement is short and general. However, the language related to California’s Shine the Light Law is very interesting. Cisco claims that their privacy policy is adequately comprehensive, and that as a result of that they do not need to maintain a list of third parties who have received information from Cisco. This is not a posture that indicates a high degree of attention to user privacy and user rights.
“Residents of the State of California, under California Civil Code § 1798.83, have the right to request from companies conducting business in California a list of all third parties to which the company has disclosed personal information during the preceding year for direct marketing purposes. Alternatively, the law provides that if the company has a privacy policy that gives either an opt-out or opt-in choice for use of your personal information by third parties (such as advertisers) for marketing purposes, the company may instead provide you with information on how to exercise your disclosure choice options.
Cisco qualifies for the alternative option. We have a comprehensive privacy statement, and provide you with details on how you may either opt-out or opt-in to the use of your personal information by third parties for direct marketing purposes. Therefore, we are not required to maintain or disclose a list of the third parties that received your personal information for marketing purposes during the preceding year.”
— — — — — — — — — — — — — — — –
Secondary Policy
— — — — — — — — — — — — — — — –
The Webex-specific document is a pdf. Best practice for sharing privacy policies generally means using valid html. It’s not clear why Cisco would choose to share a privacy document on the web in 2020 and not use valid html.
— — — — — — — — — — — — — — — –
This document states that it is a supplement to Cisco’s Privacy Statement.
Note that this Privacy Data Sheet is a supplement to the Cisco Privacy Statement.
— — — — — — — — — — — — — — — –
This document clearly describes that hosts and employers have significant ability to track employees. Because this document does not appear to be presented to employees, it is less clear how people who would benefit from this knowledge would be presented with it.
Similarly, if users participate in meetings hosted by users in other companies, the meeting host will control any meeting recordings or files shared during the meeting, which will be subject to the host’s corporate policies regarding access, use, monitoring, deletion, preservation, and export of information. The meeting host has the option to record meetings, which may be shared with others or discoverable in a legal matter. The meeting host should inform all meeting attendees prior to recording and Webex displays a red circle visible to all participants indicating that the meeting is being recorded. Note, Cisco has no control over, and is not responsible or liable for the privacy of any information that you have shared with others. Even after you remove information from the Webex Meetings platform, copies of that information may remain viewable elsewhere to the extent it has been shared with others.
— — — — — — — — — — — — — — — –
This excerpt illustrates several problems facing non-tech people (or even very technical people who aren’t familiar with every element of how Webex works, and is organized). The terms mention 4 different products under the Webex product umbrella: Meetings Suite, Events, Training, and Teams. Let’s make an enormously optimistic assumption that an average user knows the difference between these product offerings, AND knows which of these products they are using. If they happen to be fortunate and only using the three products covered in this privacy document, then they are in luck.
If, however, they are using Webex Teams, Cisco gives them a link to a page that lists (as of this writing) 81 different data sheets, and tells them to find the 1 additional data sheet that’s relevant to their product. This is an absurd amount of specialized knowledge required to find information that should be presented front and center, and this absurdly complex situation is made even worse because it’s contained in another document that should also have been front and center, but is also buried.
Cisco needs to make this information more accessible, and they should consult with UX and information architecture talent in the process. While Cisco provides a clear example here, this basic problem is common.
This Privacy Data Sheet covers the Cisco Webex Meetings Suite, Cisco Webex Events, and Cisco Webex Training. If you use the Service together with Cisco Webex Teams, see the see the Cisco Webex Teams Privacy Data Sheet (available on The Cisco Trust Center) for descriptions of the data that may be collected and processed in connection with those services.
— — — — — — — — — — — — — — — –
This secondary document — unlike Cisco’s terms that are presented to end users when they are creating their account — provides clear information about people who register for Webex.
Name
Email Address
Password
Public IP Address
Browser
Phone Number (Optional)
Mailing Address (Optional)
Geographic region
Avatar (Optional)
Billing Information
User information included in the Customer’s Active Directory (if synched)
Unique User ID (UUID)
— — — — — — — — — — — — — — — –
This secondary document — unlike Cisco’s terms that are presented to end users when they are creating their account — provides clear information about people who host and participate in meetings using Webex. Out of the three services covered in this policy overview, this is the most clear any company gets at showing data collected from hosts and participants. If this document was actually presented to end users creating Webex accounts, it would be useful.
IP Address
User Agent Identifier
Hardware Type
Operating System Type and Version
Client Version
IP Addresses Along the Network Path
MAC Address of Your Client (As Applicable)
Service Version
Actions Taken
Geographic Region
Meeting Session Information (title, date and time, frequency, average and actual duration, quantity, quality, network activity, and network connectivity)
Number of Meetings
Number of Screen-Sharing and NonScreen-Sharing Sessions
Number of Participants
Meeting Host Information*
• Host Name
• Meeting Site URL
• Meeting Start/End Time
Subscription Type
Meeting Attendee Information*
• Username of attendees
• Meeting Start/End time
• Subscription Info
Screen Resolution
Join Method
Performance, Troubleshooting, and Diagnostics Information
Call attendee information, including email addresses, IP address, username, phone numbers, room device information
* Used for billing purpose
— — — — — — — — — — — — — — — –
This secondary document also identifies these specific types of content that Cisco defines as “user generated.”
Meeting and Call Recordings
Transcriptions of Call Recordings
Uploaded Files (for Webex Events and Training only)
— — — — — — — — — — — — — — — –
If you are using Webex as part of a work-provided solution, your system administrator (and in all likelihood, your boss) can get data about how you use the system. Ideally, any information that is collected about you and your interactions would be clearly disclosed to you ahead of time.
Cisco Webex Control Hub Analytics provides usage trends and valuable insights that can be used to help with strategies to promote and optimize adoption across teams. The Webex Analytics Platform utilizes Registration, Host and Usage information to provide advanced analytics capabilities and reports.
— — — — — — — — — — — — — — — –
This document contains clear language about data portability. ̶I̶t̶ ̶w̶o̶u̶l̶d̶ ̶b̶e̶ ̶v̶e̶r̶y̶ ̶u̶s̶e̶f̶u̶l̶ ̶i̶f̶ ̶t̶h̶i̶s̶ ̶i̶n̶f̶o̶r̶m̶a̶t̶i̶o̶n̶ ̶w̶a̶s̶ ̶c̶o̶n̶t̶a̶i̶n̶e̶d̶ ̶i̶n̶ ̶t̶h̶e̶ ̶d̶o̶c̶u̶m̶e̶n̶t̶s̶ ̶p̶r̶e̶s̶e̶n̶t̶e̶d̶ ̶t̶o̶ ̶e̶n̶d̶ ̶u̶s̶e̶r̶s̶ ̶w̶h̶e̶n̶ ̶t̶h̶e̶y̶ ̶w̶e̶r̶e̶ ̶c̶r̶e̶a̶t̶i̶n̶g̶ ̶a̶ ̶W̶e̶b̶e̶x̶ ̶a̶c̶c̶o̶u̶n̶t̶.
The Service allows Customers and users to export all User-Generated Information. A Customer’s administrator may do so using APIs provided with the Service (recordings only) or through the Site Admin Page; while individual users may do so through the My Webex Page. Meeting recordings are available in proprietary ARF and standard mp4 formats depending on the account type. Cisco offers a free ARF player to convert ARF files to mp4 format.
— — — — — — — — — — — — — — — –
This document contains data retention and deletion windows that are fairly general and broad. In most cases, Cisco can retain information for up to 7 years after service is terminated. This long and open ended retention time span increases the possibility that data could be included in potential mergers or acquisitions, or product improvement, without end users having any notice, consent, or control. NOTE: because the original document is a pdf and presents the information in a table, the excerpt here changes the format — but NOT the content — of the language.
Registration Information — 7 years from when the Service is terminated — Data collected as part of registration, including information provided by Customers as part of Cisco’s financial due diligence, constitute Cisco business records and are kept to comply with Cisco financial and audit policies, as well as tax requirements.
User Generated Information — Active Subscriptions: At Customer’s or user’s discretion; Terminated Service: Deleted within 60 days — User-Generated Information is not retained on the Webex Meetings platform when Customer or user deletes this data.
Host and Usage Information — 7 years from when the Service is terminated — Information generated by instrumentation and logging systems created through the use and operation of the Service is kept as part of Cisco’s record of Service delivery. Usage information used to conduct analytics and measure statistical performance is retained but pseudonymized.
— — — — — — — — — — — — — — — –
This secondary document makes specific commitments to encryption as a means to protecting information. These commitments include clear language about data encrypted at rest, and the possibility of end to end encryption. The language around the different ways encryption is used, and how the use of end to end encryption can be implemented, provides useful clarity.
Protecting Data at Rest
The Service encrypts sensitive data at rest. Any data not encrypted at rest is protected by highly-secure data center protection mechanisms and operational procedures. Webex Meetings data centers feature communication infrastructure with industry-leading performance, integration, flexibility, scalability, and availability.
Encryption at Run Time
All communications on the Webex Meetings platform occur over encrypted channels. After a session is established, all media streams (audio, VOIP, video, screen share, and document share) are encrypted. The Service then re-encrypts the media stream before sending it to other users. Note that if a Customer allows attendees to join its meetings using third-party video end points, those attendees may be sending your meeting data unencrypted on the Internet. Media streams flowing from a user to Cisco Webex Meetings servers are decrypted after they cross the Cisco firewalls. This enables Cisco to provide network-based recording and SIP-based call support for video end points.
End-to-End Encryption (Optional)
For businesses requiring a higher level of security, the Service also provides end-to-end encryption. With this option, the Service does not decrypt the media streams. In this model, traffic cannot be deciphered by the Cisco Webex Meetings server. The end-to-end encryption option is available for Webex Meetings and Webex Support. Note that when end-to-end encryption is enabled, the following features are not supported:
• Network-based recordings
• Join Before Host
• Cisco Webex Video Platform (formerly known as Collaboration Meeting Rooms Cloud)
— — — — — — — — — — — — — — — –
This document contains details about an add-on product called “People Insights”. If you are part of an organization where this feature has been turned on and you haven’t opted out, other people in the meeting can see a broad range of personal information about you. This might not be expected behavior, and could be seen as highly intrusive. It would also support micromanaging and potential harassment in some contexts. People Insights has some superficial similarities to a feature in Zoom that was written up in the NYTimes in early April 2020, although the language describing the Webex version makes clear that the Webex version has some additional privacy protections.
The People Insights feature (“People Insights” or the “Feature”) provides Cisco Webex users with comprehensive, publicly available business and professional information for meeting participants giving users context and increased insight about the people with whom they collaborate.
Only the Customer’s site administrator has the ability to enable the Feature for their organization and users. Individual users cannot opt-in to use People Insights independently of their site administrator. Users at an enabled organization can opt-out of People Insights by suppressing their profile from other meeting participants’ view.
— — — — — — — — — — — — — — — –
The data collected by “People Insights” scours the web, including public social media profiles. The document describes using data collected from the sources listed below.
Profile Photos
News
Tweets
Authored Works
Bios
Employment History
Education History
Web Links for a specific person
— — — — — — — — — — — — — — — –
This secondary document clearly describes that Cisco has a “Facial Recognition” feature. This feature requires two levels of opt in: first, it needs to be enabled by a site administrator; and second, individual users need to explicitly opt in. In some working environments, employees could be pressured to “consent” and forced to opt in to this feature. However, the fact that this feature is disabled by default, and needs to be turned on by the site administrator, is a better way to introduce this feature. However, the usefulness of the information in this document is undercut because this information is buried in a PDF ̶t̶h̶a̶t̶ ̶i̶s̶ ̶n̶o̶t̶ ̶p̶r̶e̶s̶e̶n̶t̶e̶d̶ ̶t̶o̶ ̶e̶n̶d̶ ̶u̶s̶e̶r̶s̶ ̶a̶s̶ ̶t̶h̶e̶y̶ ̶a̶r̶e̶ ̶c̶r̶e̶a̶t̶i̶n̶g̶ ̶a̶n̶ ̶a̶c̶c̶o̶u̶n̶t̶ ̶t̶o̶ ̶u̶s̶e̶ ̶W̶e̶b̶e̶x̶.
Cisco introduced the facial recognition feature (“Facial Recognition” or the “Feature”) to provide Webex Meetings users with the ability to identify and recognize registered Webex meeting participants (i.e., associate participant names with their positions in a Webex meeting video), giving users increased connection to meeting participants. The Feature recognizes a face by converting it to an abstracted facial vector. A facial vector is a list of numbers that characterize salient facial features of a user that is then used to identify who is in the meeting. This level of abstraction allows the system to recognize the same face even when things like lighting and position change.
Facial Recognition is disabled by default, and requires affirmative action by both the customer and the user to enable. First, the administrator for the customer may enable Facial Recognition using Webex Control Hub. However, the feature will not be available on the user’s account until the user opt-ins at https://settings.webex.com. Because the Feature is based on facial vectors derived from profile images, the user must have a picture taken at the time of enablement.